Awareness
Large organizations

Large organizations are much more attractive target for cybercriminals than individuals. For that reason when you are building or considering building cybersecurity you should definitely think of having a dedicated team managing your cyber security. Such team will allow for the concentration of competences and responsibilities in one place.
Cybersecurity in your company should address at least 5 areas:
- risk assessment
- prevention
- trainings
- detection
- reaction
IN THIS SECTION
Risk assessment
Risk assessment is often associated with complex mathematical methods but in principle thanks to it you should be able to answer the following simple questions:
- What are my ICT resources which supports business processes and which of them are the most important?
- What are the most value data for y organization and in which business processes they are involved?
- What are threats to our resources and data (threat actors, threat vectors)?
- What could be the impact of losing confidentiality, integrity or availability of value data on my business processes?
To assess risk to your company you can use general risk assessment guidelines or standards such as:
You can find more useful information about risk assessment, including guidelines and good practices on webpages of the Agence nationale de la sécurité des systèmes d’information (ANSSI) – https://www.ssi.gouv.fr/administration/bonnes-pratiques/ and National Institute of Standards and Technology (NIST) – https://csrc.nist.gov/publications/sp
Prevention
Prevention is about reducing the attack surface and limiting the number of TTP (tactics, techniques and procedures) an attacker can use against us.
The most common preventive measures are hardening and training. Implementation of security tools can be considered in two roles: preventive and at the same time these tools are a source of information about a potential attack, supporting detection.
Hardening is such an approach to the configuration of systems and devices that minimizes the risk of attack. It is a process of securing given systems and devices by reducing the attack vectors (making the attack harder for attacker). There are several guidelines and good practices that provide benchmarks for various operating systems, devices and applications. Each hardening guidelines and good practices may include requirements related but not limited to:
- Physical security
- Operating systems
- Server software
- Desktop software
- Network devices and services
- Mobile devices
- Multifunction print devices
- Cloud providers
- Security metrics
For more good practices and guideline on hardening visit websites listed below:
- Center for Internet Security – https://www.cisecurity.org/cis-benchmarks/
- Defense Information Systems Agency (DISA) and known as Security Technical Implementation Guides (STIGs) – https://public.cyber.mil/stigs/downloads/
- ANSSI – https://www.ssi.gouv.fr/administration/bonnes-pratiques/
- NIST – https://csrc.nist.gov/publications/sp
Trainings
One of the very important elements supporting cybersecurity in a large organization is employee training. This enable the transfer of knowledge to employees on the safe use of ICT devices. In addition, learning about threats and methods of protection against them reduces the probability of a cybersecurity incident resulting from human error. Training should cover all employees using computer devices, including both office workers and administrators responsible for managing IT and OT infrastructure. Training should include familiarization with cybersecurity threats, basic security principles, applicable security policies and procedures in organization. Employees should also know what to do if they suspect they have been the victim of a successful cyberattack.
Detection
Detection allows you to identify potential hostile activity in your ICT infrastructure or systems. To detect potential hostile activity visibility of the current state of your infrastructure is crucial. Visibility means that all necessary information (logs) from devices, services and tools you use are collected and monitored (corelated).
Regular collection of properly selected logs enables:
- Identifying security events and incidents
- Monitoring policy violations
- Establishing baselines
Very useful tool and knowledge base for identifying threats, prevention and detection is the MITRE ATT&CK (Adversaries Tactics, Techniques and Common Knowledge). ATT&CK provides a framework for enhancing posture against specific adversaries. Thanks to ATT&CK you can find an adversary group which poses a threat to your company and identify the techniques that they are known to use. For each technique in ATT&CK you can find information on how to detect it and potentially mitigate.
For more information about ATT&CK visit https://attack.mitre.org/
If you find MITRE ATT&CK as too difficult for you – try to go through below steps.
- Data Source Identification
- what we are already monitoring
- what we can/should monitor
- Identification of threats
- what threat can we detect with the data we have
- what threat should we detect – what to start monitoring
- Forwarding the logs to SIEM(Security Information and Event Management) or other tool that offers correlating logs
- Building correlation rules – what sequence of events should be alerted
Which events to log?
Logging specific events, not necessary connected directly to security, should be proportionate to the information security risks. As a result of a risk assessment you should get general guidelines on what should be logged.
There is no one size fits all solution. For example only three data sources:
- process monitoring (information about processes, execution paths, parameters),
- file monitoring (information about created files, modifications creation times),
- process command-line parameters (parameters passed to the shell and commands),
cover more than half of MITRE ATT&CK techniques.
Below you can find not exhausted list of what you should log (if it is technically possible and justified):
- Input validation failures e.g. protocol violations, unacceptable encodings, invalid parameter names and values
- Output validation failures e.g. database record set mismatch, invalid data encoding
- Authentication successes and failures
- Authorization (access control) failures
- Session management failures e.g. cookie session identification value modification
- Application errors and system events e.g. syntax and runtime errors, connectivity problems, performance issues, third party service error messages, file system errors, file upload virus detection, configuration changes
- Network connections,
- Addition or deletion of users,
- Changes to privileges,
- Assigning users to tokens, adding or deleting tokens,
- Use of systems administrative privileges,
- Access by application administrators,
- All actions by users with administrative privileges,
- Use of data encrypting keys and key changes,
- Creation and deletion of system-level objects,
- Data import and export,
- Submission of user-generated content – especially file uploads.
Some of those logs can be collected by security tools and software like Firewall, Intrusion Detection and Prevention Systems (IDPS), antivirus software etc..
To get better visibility on you end point devices with Windows operation system consider installation of System Monitoring (Sysmon). Sysmon allows to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time.
More information on log management can be found on NIST SP 800-92 – Guide to Computer Security Log Management.
For more good practices and guideline on security tools and software visit:
Reaction
Incident response is defined as actions that an organization takes during and after a cyber incident . Incident response allows you to reduce the possible consequences of a cyber-attack and restore the functioning of the organization to the level before the attack.
The response consists of actions such as:
- identification of a cybersecurity incident
- investigation of a situation and information collection
- incident analysis
- mitigation and recovery of systems, data and connectivity
In large organizations, where the occurrence of cybersecurity incidents is very likely, a good solution is to create an entity inside the organization responsible for incident management, such as SOC (Security Operation Center). If this is not possible, it is worth considering using SOC as a Service (service outsourced outside the organization).
For more information and good practices about incident response visit:
- ISO/IEC 27035-1:2016 Information technology — Security techniques — Information security incident management: https://www.iso.org/standard/60803.html
- NIST Special Publication 800-61: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
- FIRST Framework : https://www.first.org/standards/frameworks/csirts/FIRST_CSIRT_Services_Framework_v2.1.0.pdf
- ENISA – Good Practice Guide for Incident Management – https://www.enisa.europa.eu/publications/good-practice-guide-for-incident-management
- ANSSI, Attaques par rançongiciels, tous concernés – Comment les anticiper et réagir en cas d’incident?: https://www.ssi.gouv.fr/administration/guide/attaques-par-rancongiciels-tous-concernes-comment-les-anticiper-et-reagir-en-cas-dincident/
What is SOC (Security Operation Centre)?
By definition SOC is:
The practice of defense against unauthorized activity within computer networks, including monitoring, detection, analysis (such as trend and pattern analysis), and response and restoration activities.[1]
SOC is built on 3 foundations to provide maximum efficiency of incident management, those are: people, technology and processes.
[1] C. Zimmerman, Ten Strategies of the World-Class, Security Operations Centre, The MITRE Corporation, 2014, page 8.
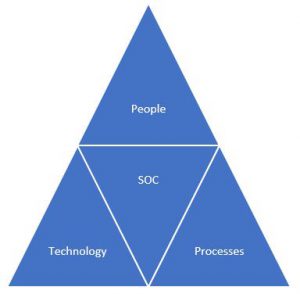
People – SOC consists of qualified security analysts, incident management specialists and experts in advanced incident analysis.
Technology – are all tools used by the team to monitor, detect, analyze and respond to incidents. The primary tool is the SIEM for event management.
Processes – a set of policies and processes defining the rules of team conduct as part of specific activities related to incident management.
What does SOC do?
SOC primarily improves threat management through overall operational management of events and appropriate response to them. Coordinated operation of SOC guarantees quick identification of incidents and their removal in order to minimize the occurring damages related to a successfully conducted attack on ICT assets.
SOC is usually divided into 3 lines of support in incident management:
1st Line – deals with routine matters, including event triage (qualification and prioritization), event monitoring in SIEM. Analysts handle or escalate events to higher lines according to accepted instructions.
2nd Line – conducts more advanced analytical processes. Except SIEM console, 2L use data and information from other systems inaccessible to 1L SOC. 2L-SOC manages cybersecurity incidents. The basic tasks of 2L include:
- handling of cases escalated by the 1L SOC;
- making decisions regarding the resolution of an incident;
- collecting and analyzing additional information;
- incident analysis and resolution, support in system reconstruction and restoration, formulation of recommendations regarding cybersecurity after an incident;
- handling the vulnerability management process;
- cooperation with the team of advanced analyzes (CTAC).
3rd Line – in large SOCs, also known as CTAC (Cyber Threat Analysis Cell), specializes in advanced cybersecurity analysis services, including:
- supports the management of threat intelligence sources ;
- conducts advanced malware analysis and forensics analysis;
- conducts red team activities;
- analyzes trends in cybersecurity threats;
- creates new tools / methodologies increasing the effectiveness of attack detection, including APT.
If you are interested in creating a SOC in your organization, please contact us to gain more information.
Work with CDA
We can help you to build cybersecurity in your company
Visit our website
Stay up-to date with the CDA’s advisories relating to cyber security matters affecting the Togolese Republic and Africa.



